Networks
Uncover the principles of computer networks and how they enable communication between devices. Learn about different networking methods and protocols that keep our connected world running smoothly.
Contents
A network is formed when two or more computers are connected together.
When computers are networked, it allows them to share data and resources. For example: data such as an email can be passed between different computers on a network, or a printer can be accessed by many by multiple computers without a direct connection.
There are many different types of networks, all of which serve different purposes.
The terms Local Area Network (LAN) and Wide Area Network WAN refer to the physical area a network covers.
Local Area Networks
A Local Area Network (LAN) covers a small geographical area such as a building. All the hardware that makes up the LAN is privately owned, e.g. the company using the LAN owns the LAN.
Examples of LANs include:
- Businesses
- Schools & Colleges
- Your own home
LANs can include wired and wireless devices.
Wide Area Networks
A Wide Area Network (WAN) connects LANs and computers over large geographical locations. WANs are owned by companies and access is rented or leased to its users (think about how people must pay for internet access).
Examples:
- The Internet - the largest WAN
- VISA / MasterCard - payment providers which use their network to authorise digital payments
- Military - they use WANs to provide secure communication between their difference bases of operation.
WANs connect devices and LANs using ethernet, fibre, satellite and phonelines.
There are two models of how computers share resources on a network: Client-server and Peer-to-peer.
Most of the time this comes down to whether you want to use a server.
What is a Server?
A server is a computer which provides resources for other computers. Sometimes servers have to be very powerful and sometimes they may look no different from a regular desktop computer. Additionally, the server can occasionally provide more than one type of resource.
Client Server Networks
Client-server Networks are managed by servers.The server provides services to other computers on the network – this could be file management, access to printers, user access security. Schools use a client-server model: school servers store our files, manage us logging into computers, manage update and back-up and printing.
Benefits
- Central file storage: easier to back-up and access files from multiple computers.
- Managed security: password policy and network rules.
- Reliable: servers are always on and resources/files will be available 24/7.
Drawbacks
- More expensive (requires expensive hardware).
- Requires experts to set-up and maintain.
Peer-to-Peer Networks
On a peer to peer network, all the computers are equal (no singular computer is more important than the rest). There is no server, so all computers share files and resources between themselves. Most home networks are Peer to Peer.
Benefits
- Inexpensive (doesn’t require expensive hardware or a server).
- Easy to set-up (doesn’t require expertise to set-up).
Drawbacks
- Slows down as more computers are added.
- Less reliable: resources and files can become unavailable if a computer fails)
- If computers are off their files and resources won’t be available on the network).
To connect computers together, you need specialised hardware. The most common hardware devices are:
- Network Interface Cards
- Switches
- Routers
- Wireless Access Points
Network Interface Card
A Network Interface Card (NIC) is hardware built into computers and allows them to connect to a network.In the past NICs were not built in and were optional expansion cards.

NICs can be wireless (to connect via WiFi) or wired (to connect via ethernet). NICs can be rated for different speeds, for example: a Ethernet NIC could be capable of different maximum speeds: 10 MB/s 100 MB/s , 1 GB/s, 10 GB/s , etc.
Switch
A network switch is used to connect devices together and it is often described as the central networking device. Devices are connected to a switch using Ethernet Cables. When a device sends data to another device, the data is received by the Switch and then directs that data to the device it is meant to.

Switched make use of MAC addresses to direct network traffic.
Most run at 100MB/s (Megabit / second) or 1GB/s (Gigabit / second)
Router
Routers sit between two different networks and allow communication between them. Most often routers connect a LAN (Local Area Network) to the Internet (an example of a Wide Area Network)
Routers make use of IP Addresses to route data between networks.
Routers are a crucial internet device and transfer data packets between different privately owned networks that make up the internet
Wireless Access Points

Wireless Access Points (WAP) allow devices to wirelessly connect to a network via WiFi. WAPs connect directly into a switch, and many can be powered directly over PoE (Power over Ethernet).
All the ways we can connect computer together can be categorised as Wired or Wireless
- Wired connections physically connect the computers together to transfer data
- Wireless connections use radio frequencies to transfer data without a physical connection.
When picking or comparing connectivity methods we need to consider: Speed / Bandwidth, Range, Latency
Wired connections make use of cables and there are two main types: Copper Cables and Fibre-optic Cables.
Copper cables
Copper cables are the most common type of cable. Pulses of electricity are used to transmit data (as 1s and 0s).
- Speed / Bandwidth: most wired copper connections used on a LAN will be capable of providing 100MB/s - 1GB/s bandwidth
- Range: ~ 100m, after which the electrical signal will need to be repeated and re-amplified
- Latency: Higher than that of a fibre-optic cable
The most common copper cable used in networking is the CAT 5 / CAT 6 cable, which is often simply referred to as an Ethernet Cable. Copper cabling is most commonly used due to being inexpensive and having a wide compatability.
Fibre-optic Cables
Fibre-optic cables are becoming more common, especially in WANs. They use pulses of light to transmit data.
- Speed / Bandwidth: capable of providing large amounts of bandwidth, greater than that of a copper cable.
- Range: many miles. Due to total internet reflection, the light signals sent down a fibre-optic cable can travel many miles without error.
- Latency: Less than that of a copper cable
They provide greater bandwidth, range and latency than copper cables, but are generally too expensive to be used on LANs.
Broadband
Over the past 10 years Internet Service Providers (ISPs) have been upgrading their networks replacing copper cabling for fibre-optic cabling to provide higher performance broadband.
There are two approaches:
- FTTC (Fibre to the Cabinet): Fibre-optic cabling is laid to the cabinet, and copper cabling is then used to connect the cabinet to the property
- FTTP – Fibre to the Property: Fibre-optic cabling is laid to the cabinet, and fibre cable is laid from the cabinet to the property.
Fibre to the property is more expensive and is more likely to be used by business.
Microwaves and Radio waves are used to transmit binary data. The binary data is represented by pulses of electromagnetic frequency.
WiFi and Bluetooth are the most common protocols for transmitting data wirelessly, however newer protocols have appeared in recent times such as Thread and Zigbee which have become popular in low power home automation. These protocols set the rules for how data is sent and received by devices.
The main benefit of using wireless connections is the convinenece of not having to be tethered by a cable.
Limitations of Wireless Connections
While wireless connections are convienent there are many limitations:
- Range: While a wired connection can carry a signal at least 100m over CAT 5 / CAT 6 and much further over fibre-optic cables, the most common methods of wireless networking have shorter ranges. WiFi has a limit of 30m and lower power protocols like Bluetooth has an even shorter range.
- Bandwidth: More recent versions of WiFi boast bandwidth figures greater than that of wired connections, however in reality the amount of bandwidth available is much lower and less than that of a wired connection in almost all situations.
- Interference: Wireless connections are suseptable to interference from other wireless connections and frequencies in the imediate area. This interference may require error correction or that data packets to be resent. The more common frequencies such as 2.4GHz that is used by WiFi and Bluetooth experience interference from Microwave ovens and baby monitors which also make use of 2.4GHz frequencies.
- Absorption, Reflection and Refraction: Wireless signals can be absorped, reflected and refracted when they come into contact with different physcal materials. This can result limited range and areas of buildings where devices cannot connect to the network.
Wirless Local Area Networks (WLAN)
WLANs make use of Wireless Access Points (WAP) – these are devices which allow wireless devices to join a LAN using WiFi.
At home your WAP is integrated into a multi-function devices commonly referred to as the "router”.
In commercial settings a WAP is a separate device. In larger buildings a network may have many WAPs in order to provide wider wireless network coverage.
Other forms of Wireless Connections
While WiFi and Bluetooth are the most widely known forms of Wireless Connections, there are a range of other technologies we use in our daily lives.
- RFID (Radio Frequency Identification): A short form of wireless communication (usually >10cm). This technology is often used in ID cards to open electronically locked doors and with contactless debit and credit cards. RFID is unidirectional with data being read off the RFID chip.
- NFC (Near Field Communication): Similar to RFID, however data can be sent bi-directionally and at faster rates. NFC can be used to share data between devices at short distances (again, usually > 10cm). NFC is used in mobile contactless payments: the terminal sends data to the smartphones NFC chip, and if authenticated by the user on the device the payment details are sent to the payment terminal.
- Zigbee: A 2.4GHz radio protocol used in smart home hardware to connect devices. Zigbee can be used to create mesh networks which allows devices to pass data on for devices which may be further away from the base station.
Topologies refer to how networks are physically set-up (how they are all connected with wires or wirelessly).
There are many topologies, many of which that are no longer used. We are going to cover 3 main ones covered by the different Computer Science specifications.
- Star
- Bus
- Mesh
Star Topology
On a star topology network all devices are connected to a central switch. A common misconception is that computer connect directly to a server, however servers connect to the switch just like every other device on the network.
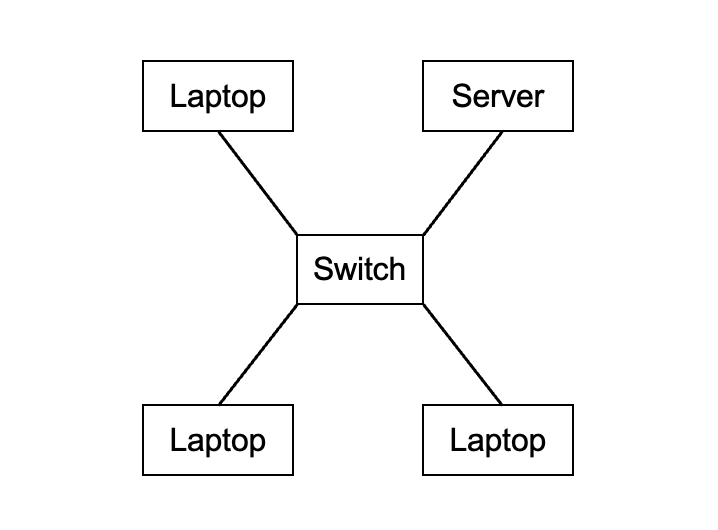
Computers can be connected via wires or wirelessly (when using a WAP).
Benefits
- If one computer fails, the rest of the network continues to function.
- Each computer has a dedicated line to the switch and doesn’t share its bandwidth with theother computer.
- Easy to add a computer to the network (new computers simply plugged into the switch using a cable)
Drawbacks
- Requires a switch, which can be expensive on larger networks
- Switch is a single point of failure (if it breaks down you don’t have a functional network).
Mesh Topology
On a mesh networks computers connect to each other without a switch, often making multiple connections to different computers.
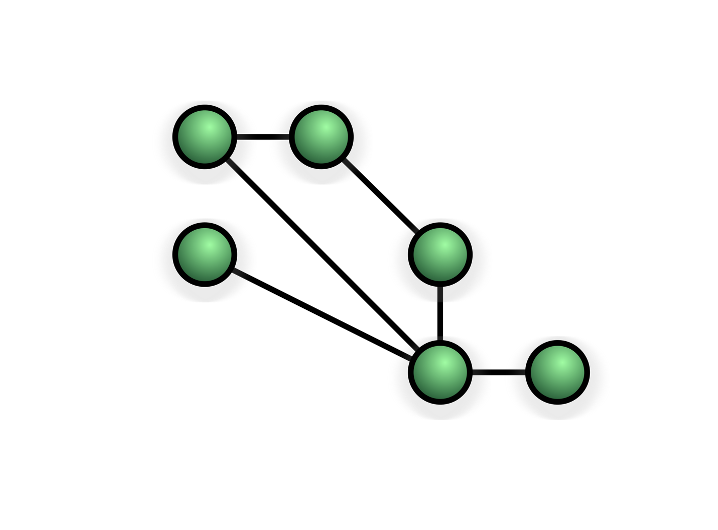
Sometimes all devices on the network will be connected to every other device (full mesh) and other times they connect through each other (partial mesh - shown above).
Benefits
- No single point of failure
- Computers failing will not impact data being sent to other computers
- Very reliable due to multiple routes to every computer
Drawbacks
- Expensive if connected with wires
- Cannot be set-up without an expert
- Difficult to maintain
Bus Topology
On a bus network all computers are connected to a single cable and at the end of the bus network cable is a terminator – this stops the signal on the cable being reflected back. This is an old topology which is no longer used – it has many disadvantages compared to modern topologies.
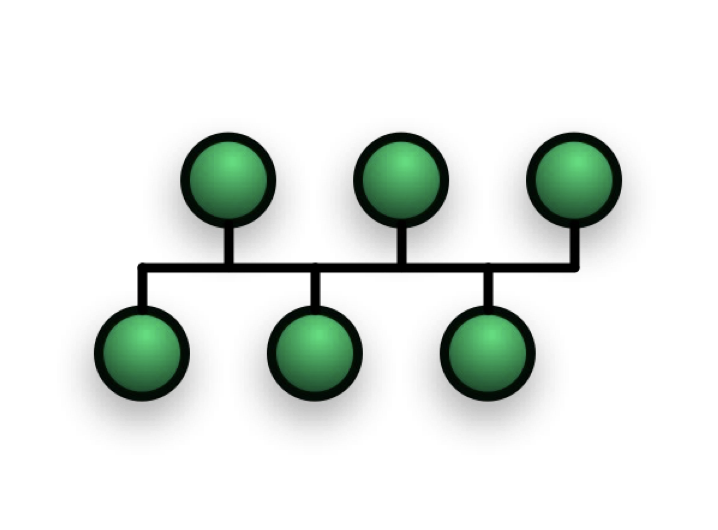
Benefits
- Easy to add a computer to the network
- Low cost – requires less cabling than a star or mesh topology network
Drawbacks
- All computers sharing the cable means that the network will not scale well with additional computers
- If there is a break in the bus network cable all of the computers will not be able to use the network
- Every computer on the network receives all data – this can be a security risk
Protocols are a set of rules for how computers communicate.
They stipulate:
- How communication starts
- How communication ends
- How the sent data is organized
- What to do when there’s an error
- How to resend data if there’s an error
Without protocols computers could receive data but wouldn't know what to do with it. If all computers follow the protocols communication should work with few issues.
There are thousands of protocols which manage different types of digital communication between devices, however the commonly used ones are:
- HTTP: Used by web browsers and web servers to manage website requests and sending web pages and connected resources in response to the requests.
- HTTPS: This has the same purpose as HTTP but uses encryption to protect the contents of the request and any data sent in response.
- POP: Is used for receiving mail from an mail server. It downloads all the messages on the server and then deletes them off the server. POP is an old protocol and was beneficial when server storage space was costly.
- IMAP: Is used for receiving mail from a mail server. It synchronizes mail between multiple devices and the mail server. The devices and mail server contain copies of the same data.
- SMTP: Used to send from a computer to the mail server or between mail servers.
- FTP: Used for transferring files from a computer / client to a server. Sometimes files can be transferred between clients / computers.
- IP: Responsible for how the packets move between networks (managed by routers). Uses IP addresses to identify the sender and destination.
- TCP: Responsible for splitting data into packets, re-ordering packets when received and ensuring all packets are received.
- Ethernet: Manages how data is physically transmitted down a cable.
Network communication is very complicated. To simplify things we break down different parts of the communication into four layers.
A single protocol must only work at a single layer and each one manages a different part of communication and thus groups similar protocols together.
We call the layered system the TCP/IP Stack.
The Layers
- Layer 4 - Application: Called application because this is the level that user software works at. Protocols on this layer format the data to be sent correctly or unpackage the formatted data to be used when received
- Layer 3 - Transport: Breaks down the formatted data into packets. Numbers the packets so they can be put back in order. Checks all packets are sent and received. Identifies how the computer should deal with the data using Ports (port numbers identify which kind of application the data should be used by)
- Layer 2 - Internet: Manages making the connections between different Networks. Used by routers to pass data between networks.
- Layer 1 - Link: Manages how the data is sent over cables or wireless signals
How the TCP/IP Stack works
Benefits of using Layers
- Protocols in each layer are self contained and don’t need to consider what other layers are doing. If someone was to create a new online game which passes data between different players, they only have to worry about working with one layer.
- Protocols can be changed within a layer without re-writing the layers above and beneath it. We can swap HTTP with HTTPS in the application layer without re-writing how data is sent down a cable or how the data is broken apart into packets.
We need a way of identifying computers so data can be directed to the right one, and when that computer responds it knows where the data came from.
Every packet contains a destination and source address.
There’s two ways of identifying a computer on a network:
- IP Addresses
- MAC Addresses
MAC Addresses
When sending data between computers on a LAN we use MAC Addresses. Every Network Interface Card (NIC) has a hard coded unique MAC address.
This address is a 48bit or 64bit binary number, but it is shown in a more human-friendly hexadecimal number.
A device with more than one method of connecting to a network will have multiple unique MAC addresses (one for each connection method).
If there is a situation where two devices had the same MAC address, it would cause a wide range of network errors.
IP Addresses
IP Addresses are needed for communication between different networks. The internet and home networks are based on the IP protocol.
They are either 32bits (IPv4) or 128bits (IPv6) wide. We display IPv4 using denary numbers to make them more user friendly:
IPv4: 51.114.200.99
They can be dynamic or static:
- Static – A computer gets the same IP address each time it connects to the internet
- Dynamic – A computer gets a different IP address each time it connects to the internet
We mainly use IPv4 addresses, but we have run out of useable addresses.
We have managed by using dynamic addresses and only assigning IP addresses when a device connects to the internet.
Eventually, to continue adding devices to the internet, we will have to (slowly) continue transitioning over to IPv6.
We should never run out of IPv6 addresses: there are enough to give every grain of sand on Earth an address and still have plenty left over!
Many of the files we send over a network are far too big to be sent in one go. Instead, we break them down into smaller manageable units called packets.
When receiving, for example a website, the website will be able up of thousands of individual packets
Each packet contains additional information to support the data being received and reassembled in the correct order.
- Sequence number
- Checksum
- Type of packet
- Addresses (sender & destination)
This data is stored in the header
Packet Switching
When sending packets over a network, or the internet, a series of steps take place. The below example using a webpage outlines the steps.
- You request a webpage
- The web server receives the request via the internet
- The webpage is broken down into smaller parts (packets)
- The packets are sent across the internet to your IP address. These packets may take different routes and arrive in a different order to that they were sent
- Your computer reassembles the packets into the website.
- If any packets are missing your computer requests the missing data.