Cyber Security
Learn about the various threats to computer systems and the essential strategies to prevent them. Dive into the world of cyber security to protect your digital life and data from malicious attacks.
Contents
Cyber-attacks are ever more frequent and a lot of effort goes into both preventing and dealing with the consequences when they have happened.
Understanding the motivation behind attacks can help organisations understand more about the risks they face so that they can tackle them.
The main reasons behind an attack are:
- Financial Gain - targetting sensitive information which can be sold or used for blackmail.
- Data and Information Theft - targetting data which may be valuable, e.g. to a competing business or to another government
- For fun - not motivated by money, but for the thrill of carrying out an attack. Individuals carrying out attacks for fun aim to gain notoriety within their communities
- To disrupt business activity - aiming to disrupt a business to prevent them from providing a service to their customers.
- Personal attacks - driven by personal vendettas against a business or individual. They could be a disgruntled former employee or customer
Malware is Malicious Software that causes damage. Once on a computer they can delete files , change files, copy files, and even encrypt files.
Types of malware
There are many types of malware and one piece of malware can be categorised in many ways:
- Viruses Infects files, and runs when the user operates the file. Will spread to other file. Requires human interaction to spread
- Worms Much like viruses but can self replicate without human interaction.
- Trojan Disguises itself as a different or useful file in order to get a user to download or operate it.
- Keyloggers Tracks what the user is typing on their keyboard to steal passwords and personal information.
- Ransomware Locks a computer by encrypting files. Usually shows up a ransom screen demanding money in exchange for access to the locked files.
- Adware After infecting the users computer it displays adverts on the screen using pop-ups, or by injecting them into web pages.
How does malware get onto a computer?
Malware can get infect a computer in numerous different ways including from the user downloading unknown files, downloading e-mail attachments, opening files from external storage, or from other computers on the network. Viruses could also be installed intentionally as well as accidentally.
Anti-malware
Anti-malware software (AKA Antivirus) scans a computers files and any incoming files. The files are compared to a database of virus signatures. If the file matches a signature in the database then it is identified as a virus. Anti-malware software must be kept up to date so that new viruses can be identified.
Sometimes called Man in the Middle attack or Passive attack, the attacker monitors data being sent over a network. The data being sent can be read and it may contain passwords, sensitive information, credit card details etc. Usually the attacker does not modify the data so the victims don’t realise it is happening.
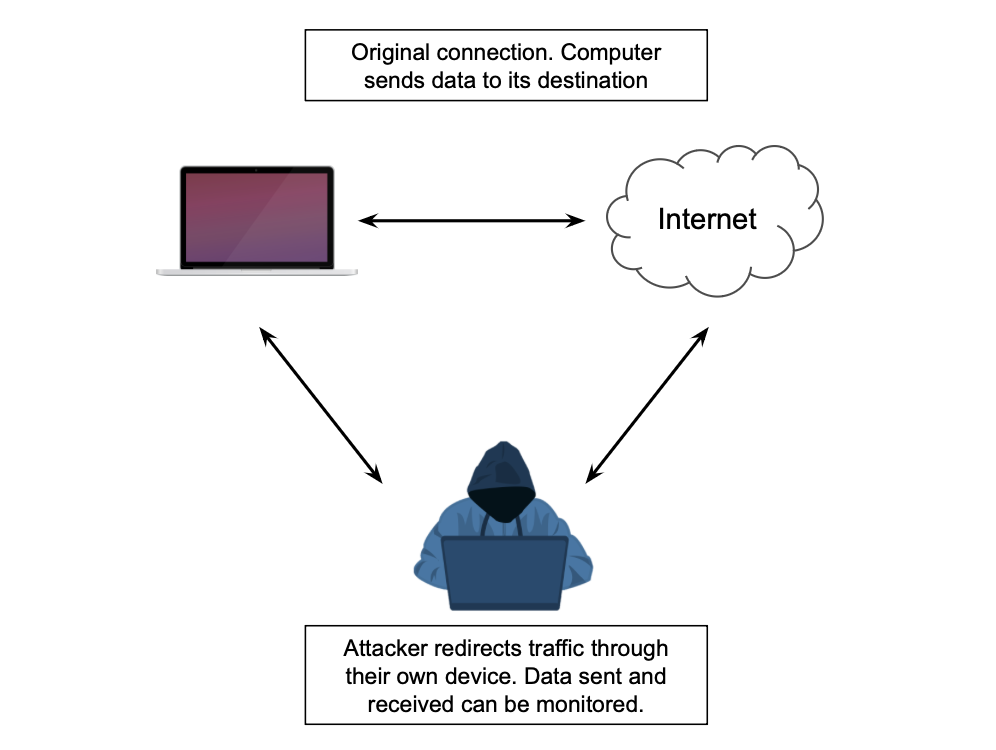
Data interception cannot be prevented however the risks can be mitigated by using encryption to stop the data from being read.
A computer and network could have every possible protection but the most difficult vulnerability to fix is us (humans). Social Engineering is convincing a user to compromise the security of a computer or network For example: Tricking a user to use a USB Flash drive which has a virus or calling someone up to trick them into giving them remote access to a computer. There are four types of Social Engineering: Phishing, Pre-texting, Baiting and Quid Pro Quo
Phishing
Phishing is an example of Social Engineering where the attacker sends out e-mails pretending to be a trustworthy company or person. The e-mail will try to convince the user to click a link and this may lead to a page with a virus download or a website which attempts to trick the user into giving up personal information.
Pre-texting
With Pre-texting, an attacker will manipulate a victim by telling them a story as to why they need to divulge information. The story is used to help the attacker gain the victims trust. Examples:
- Receiving a call from someone at “Microsoft” and requesting login details to fix an account.
- Receiving a text from someone claiming to be a family member with a new telephone number.
Baiting
Baiting is where a hacker will use a false promise to entice a user into giving up information or into installing malware. For example: Leaving USB drives outside buildings in the hope that one will be taken inside and plugged into a computer
Quid Pro Quo
An attacker will offer an exchange often information in exchange for money. Usually the attacker will not pay the victim - remember if an offer seems too good to be true it probably is!
Prevention
The best way to defend against Social Engineering within an organisation is through the use of an Acceptable Use Policy (AUP). The AUP is a document which contains a set of common rules and procedures. Typically within an organisation everyone using IT equipment have to agree to and abide by the AUP.
Hacking is the act of gaining unauthorised access to a computer. A hacker will break in by circumventing security, they may know someones password, or they may have found weaknesses in software that allow them to access the computer.
Once a hacker has access to a computer they will be able to access the data on it as if they were an authorised user.
Hacking may take place remotely or even directly on the computer.
The most common form of hacking is someone simply logging onto a computer with someone elses username and password. This is why it is important to have a strong password that no one else knows.
Not all hackers are malicious, some hackers can be ethical, and work to help organisations defend themselves from malicious hackers. These ethical hackers may be employed to break into an test the security features of a computer system. They report any issues they find so that they can be addressed.
This is called penetration testing

We use a coloured hat system for identifying what kind of hacker someone is.
- White hat hackers are ethical hackers and carry out their activities with permission (authorised access)
- Grey hat hackers are ethical hackers but will hack systsems without permission. They may hack a system to bring attention to a security problem, or for a "bug bounty".
- Black hat hackers are malicious hackers
A firewall is a tool which allows us to protect a computer. Firewalls monitor and block incoming and outgoing connections to a network. A firewall can be software that is installed on a computer, but for larger organisations can be a hardware appliance. To defend against hackers outside of the computer system the firewall can block their incoming connections. If the hacker is inside the system a firewall may prevent data leaving the network
Encrypting stored data and data being sent over a network decreases the likelihood of data being stolen and accessed using a Man in the Middle attack.
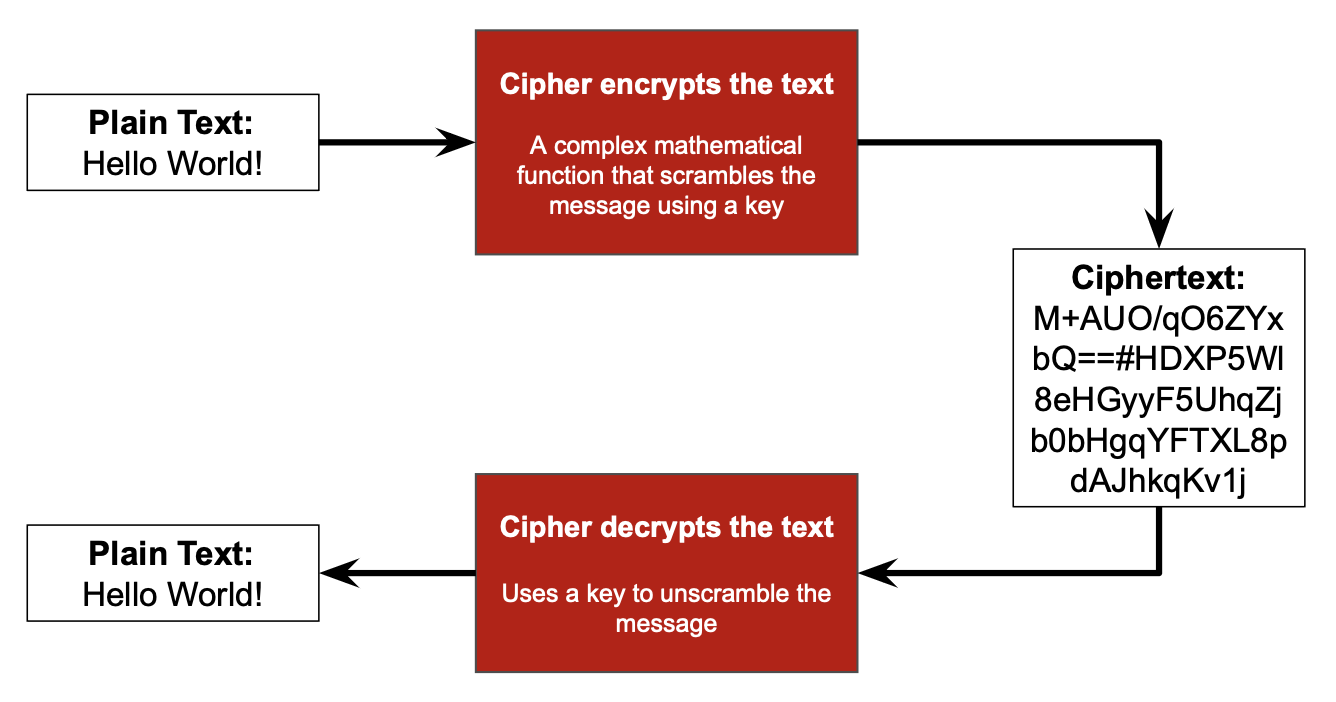
Encryption requires the use of ciphers - algorithms that use keys to scramble data (and then unscramble them to decrypt the data)
When encrypting data the "plain text" is ran through a cipher which, using a key, scambles the data. This scrambled data is referred to as "cipher text". This "cipher text" can be decrypted by someone with the cipher and the correct key.
Caesar Cipher
One of the earliest cipher used was the Caesar Cipher, named after Emperor Caesar who used a cipher to encrypt private and confidential messages.
The cipher is very basic using two rows of letters from the alphabet. One of the rows is shifted and the message is passed through the cipher matching the letters from the message using the top row and then writing down the letters on the bottom row.
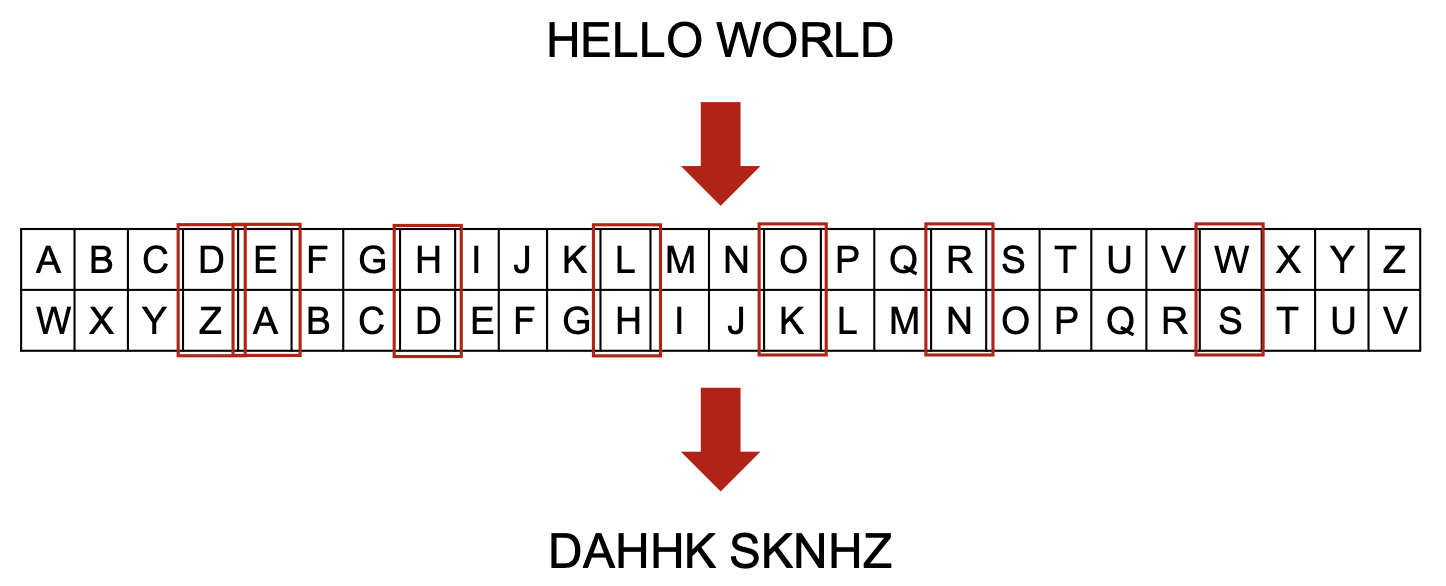
This process can be reverse so once the message has been received it can be decrypted. The recipient must know how many places the cipher has been shifted.
Caesar Ciphers are no longer secure and could be defeated by a computer in a matter of seconds. Most ciphers we use nowadays would take a single computer millions of years to defeat through brute force.
A penetration test (or Pen Test) is carried out by a professional security specialist hired by a company to attack their computer system in a similar manner to a real hacker.
After the penetration test the professional will generate a report highlighting areas of weakness so that the company can improve their security.
Policies are rules which users of a computer system agree to follow.
The aim of policies is to eliminate human error by limiting what the users can do and identifying how they should act when using computers.
Policies may include:
- Strength of password
- Limiting access to USB devices
- Limiting access to websites
- Limiting installation of software
Users may have to agree to an Acceptible Use Policy which will outline what they can and cannot do on an organisations computers and network. Some network policies can be enforced by the computers for example a computer can prevent a USB drive being accessed by a user if it is set up correctly.
Network policies can also be enforced at different levels using User Access Control.
On a network, users can have different levels of access to control what they can view, edit, and delete. Set-up correctly, user access levels can prevent lower level employees accessing sensitive information, or prevent users accidentally deleting data. In School we use access levels to protect data. Students can only access and edit their own files, Teachers can access and edit student files, their own files, and edit files on shared drives. Without access levels anyone within a school would be able to access any files on the network.
Sometimes an attacker me simply steal or take a computer or device. Computers can by physically attached to furniture or the building to prevent it being stolen. K Locks are a common way to attach laptops, which are easier to steal, to furniture such as tables. Some types of computers, such as servers, might be attached a rack which can be physically bolted to the floor to prevent them from being taken.
Organisations can also put additional physical barriers in place such as locked doors, electronic key card doors, or doors which operate with NFC to prevent unauthorised people accessing computers which contain confidential or personal data.
Most computers and networks are protected by passwords.
A brute force attack is where an attacker guesses usernames and passwords in order to gain unauthorised access to a computer system.
Carrying this out manually using a keyboard to manually enter passwords could take an attacker their entire lifetime to successfully break into a system, however specialist software on powerful hardware is capable of making millions of password guesses every hour.
This can render weak and common passwords ineffective at protecting systems.