Data Interception
Contents
1. Data Interception
Sometimes called Man in the Middle attack or Passive attack, the attacker monitors data being sent over a network. The data being sent can be read and it may contain passwords, sensitive information, credit card details etc. Usually the attacker does not modify the data so the victims don’t realise it is happening.
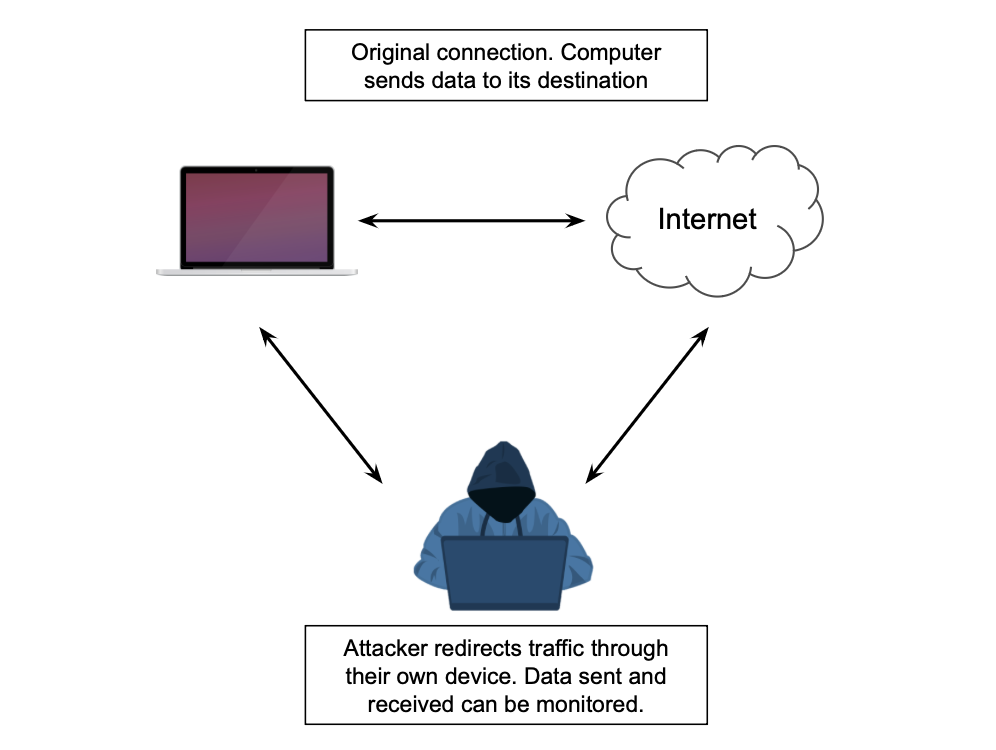
Data interception cannot be prevented however the risks can be mitigated by using encryption to stop the data from being read.
2. Encryption
Encrypting stored data and data being sent over a network decreases the likelihood of data being stolen and accessed using a Man in the Middle attack.
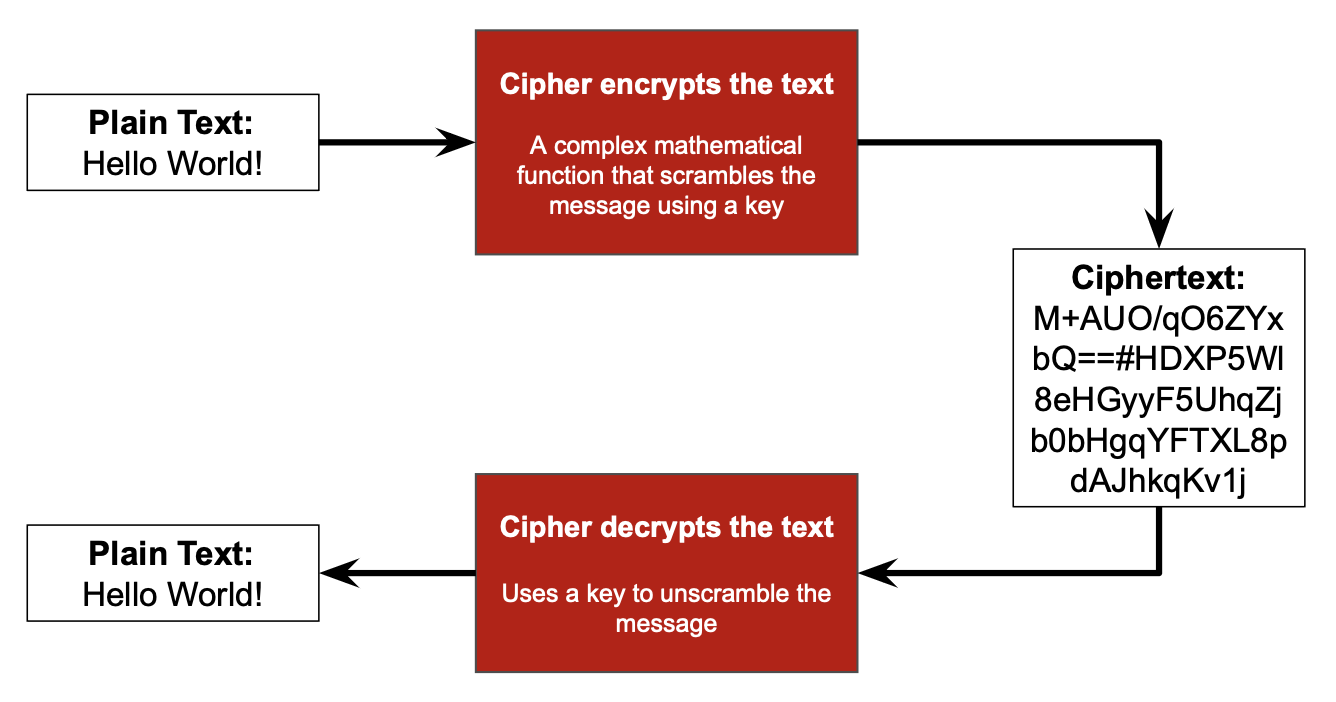
Encryption requires the use of ciphers - algorithms that use keys to scramble data (and then unscramble them to decrypt the data)
When encrypting data the "plain text" is ran through a cipher which, using a key, scambles the data. This scrambled data is referred to as "cipher text". This "cipher text" can be decrypted by someone with the cipher and the correct key.
Caesar Cipher
One of the earliest cipher used was the Caesar Cipher, named after Emperor Caesar who used a cipher to encrypt private and confidential messages.
The cipher is very basic using two rows of letters from the alphabet. One of the rows is shifted and the message is passed through the cipher matching the letters from the message using the top row and then writing down the letters on the bottom row.
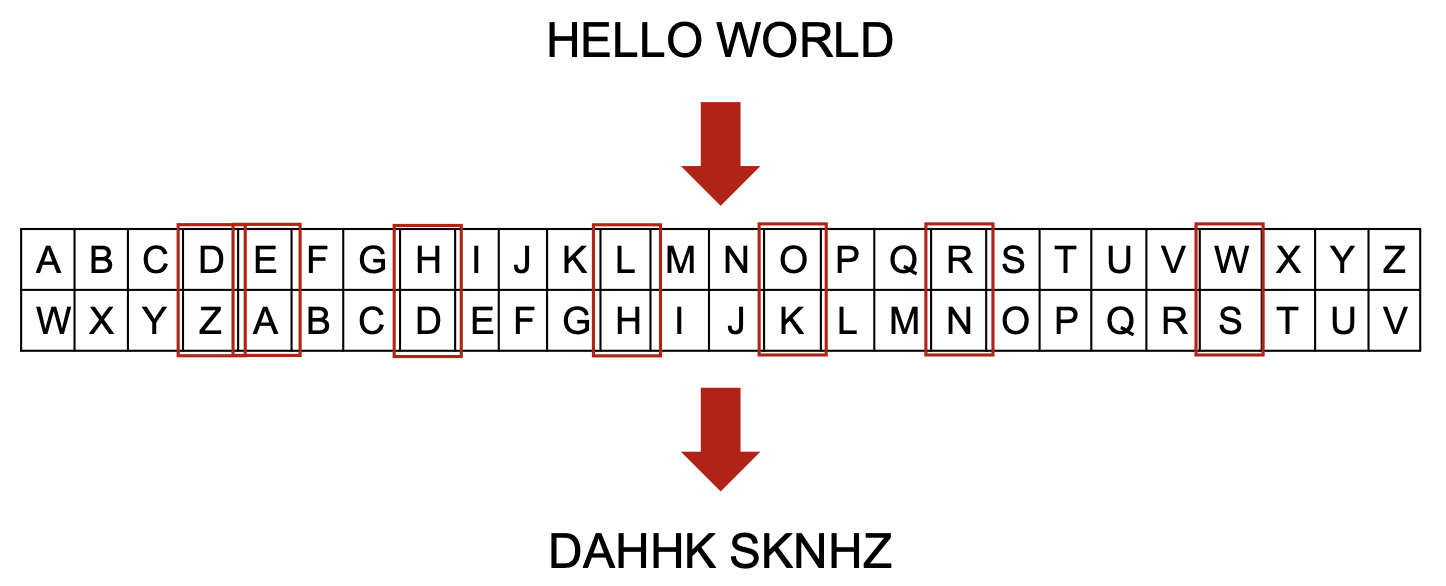
This process can be reverse so once the message has been received it can be decrypted. The recipient must know how many places the cipher has been shifted.
Caesar Ciphers are no longer secure and could be defeated by a computer in a matter of seconds. Most ciphers we use nowadays would take a single computer millions of years to defeat through brute force.