Utility Software
Contents
1. Utility Software
Software required for maintaining the computer. Without utility software the computer may become unstable, or run “slower” over time. Some utilities can run automatically, some are manual.
2. Utility Software: Encryption Software
Encryption is the process of using an algorithm called a cipher to scramble the data in such a way that it would be very inconvenient to unscramble. Encryption algorithms use keys (essentially a password) to uniquely encrypt data. This key is needed to decrypt the data.
Encryption software is used by a computer in two different ways. Firstly many operating systems use "full disk encryption" to protect their users files, this prevents an attacker with local access gaining access to the files on the computer. Encryption software is also used to encrypt data in transit, for example: a web browser will use encryption software to encrypt web requests before they are sent across the internet to a web server.
3. Utility Software: Compression Software
Compression a process that reduced the size of a file.
When we use compression software to :
- Maximise the use of secondary storage devices by lowering the amount of data we have to store for each file.
- Minimise the amount of time it takes to send a file over a network by reducing the number of bytes that have to be sent.
There are two types of compression: Lossy & Lossless.
4. Utility Software: Disk Defragmenter
Traditional hard disks store data physically on a magnetic platter and this data is read by moving a magnetic head across the disk (it physically moves). The operating system attempts to store all parts of the file contigiously (all together) in adjacent sectors.
Over time files get deleted and it creates gaps of free space on the hard disk. When new files are written to the disk it may have to fit parts of files in-between others. Storing a file across different parts of a hard disk is called “fragmentation”.
When we need to open and access a fragmented file the head must physically move to retrieve all the parts of the file, this can slow down opening or accessing of a file. When a file is not fragmented, the head doesn’t need to skip over different parts of the hard disk, speeding up the processing of opening a file.
Defragmentation software attempts to reorder how files are stored on a hard disk, placing parts of fragmented files back together and storing them contigiously.
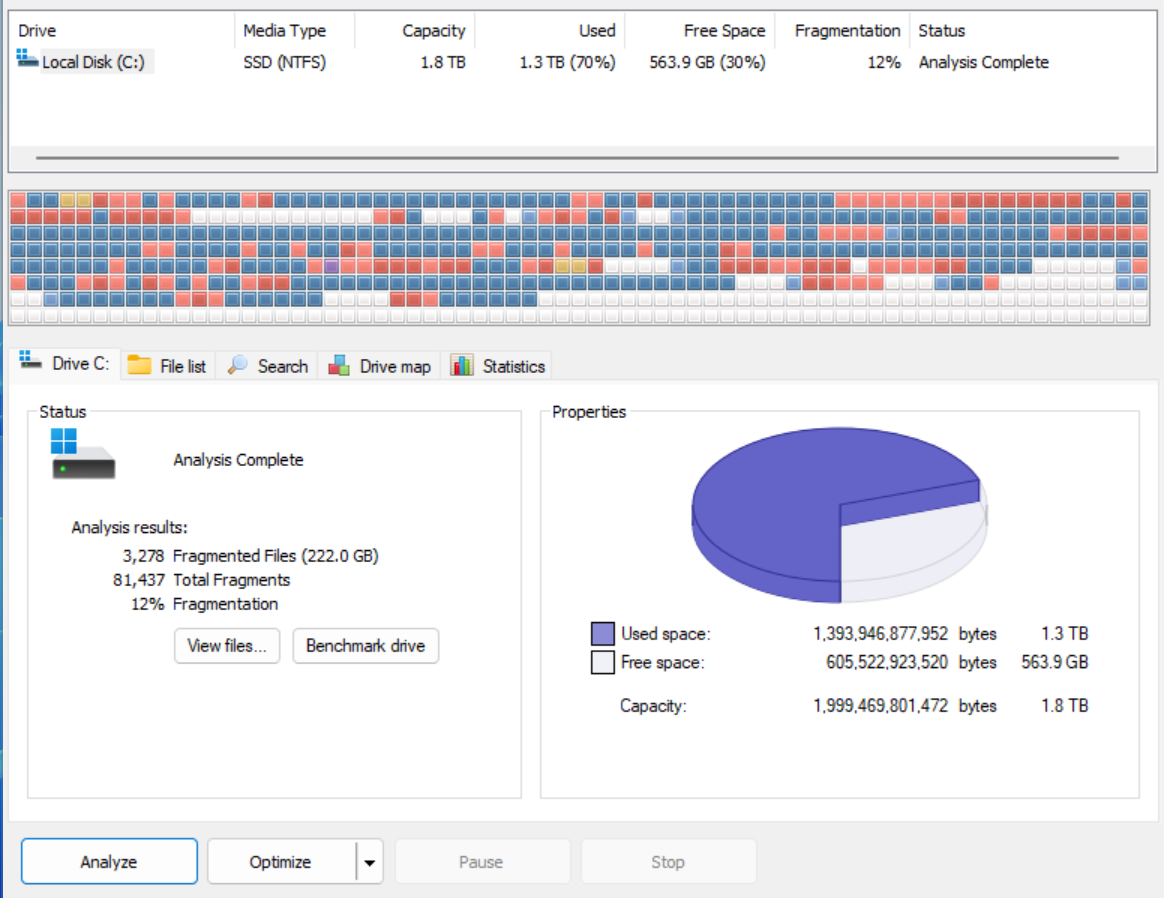
Firstly the defragmentation software will gather all of the free space on the disk together, this will give the software space to move files around the disk. The software will then attempt to move file fragments around until as many files can be stored contigiously as possible.
Once complete it will improve the speed at which those previously fragmented files can be accessed.
Defragmentation software should only be ran on magentic hard disk drives as there is no performance benefit on an SSD of storing files contigiously.
5. Utility Software: Back-up
Back-up software is used to create copies of files incase the original files are lost, damaged or deleted. This process is essential in situations where data can be accidently deleted, or data could be lost to some from of cyber security issue.
There are two types of back-up:
- Full Backup - A full back-up will duplicate all files on the computer. It is the simpliest way to back-up and subsequently restore files on a computer. However the process is slow and requires large amounts of disk space for each subsequent back-up due to duplication.
- Incremental Backup - An incremental back-up initially runs a full back-up the first time it is ran, however each subsequent back-up only duplicates new or modified files. This reduces the time each back-up takes and saves on disk space. This process will cause slower restoration of files due to increased complexity.
6. Utility Software: Anti-malware
Anti-malware software (AKA Antivirus) scans a computers files and any incoming files. The files stored in secondary storage are compared to a database of virus signatures, if the file matches a signature in the database then it is identified as a virus and can then be removed.
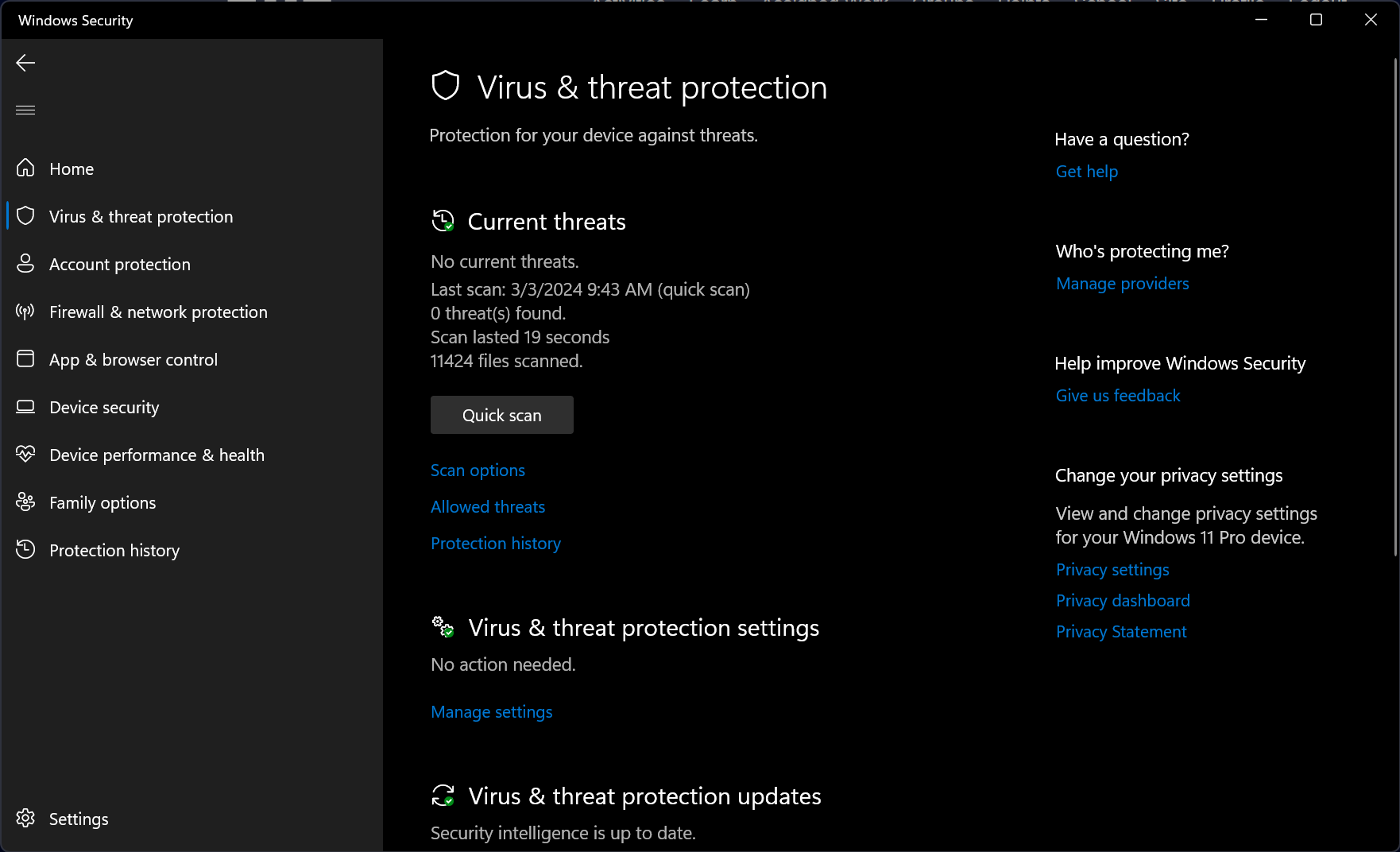
Anti-malware software must be kept up to date so that new viruses can be identified, however the software can also carry out heuristic analysis to identify malware that has not yet been identified. There's two types of heuristic analysis:
- Static analysis: decompiles a file and reads it’s source code - this is compared to known virus source code and if part of it is matched it is flagged as a virus
- Dynamic analysis: runs the file in a controlled “sandboxed” environment and is monitored for its actions. If it duplicates or alters files it is flagged as a virus.
Many anti-malware applications will use bothsignature and heuristic analysis to provide the greatest chance of protecting a computer